Content

1.4 Tbps DDoS, Largest attack to date, successfully defended
In October 2024, Link11 was confronted with one of the largest DDoS attacks ever registered on the Link11 network. The attack reached peak values of 1.4 terabits per second (Tbps) and 120 million packets per second (Mpps). It was not based on sophisticated attack techniques, but on sheer volume. Despite the enormous load, the attack was successfully repelled in its entirety, and the customer’s services were maintained without interruption.
A look at the numbers: the sheer volume of the attack
DDoS attacks in Europe are becoming more frequent. Attacks of this size raise the question of how Europe can defend itself against DDoS attacks. As overall network capacity continues to grow, volumetric attacks remain popular to leverage this capacity.
A 1.4Tbps attack is the equivalent of streaming more than 300,000 HD videos simultaneously. Such a data flow overloads the network and server CPUs. Today, DDoS protection must be designed to be automatic and agile, as real-time responses are necessary and manual intervention or pure filter solutions are no longer sufficient for large amounts of data.
Attack details: A complex strategy
The DDoS attack used a variety of attack vectors, making the defense measures significantly more difficult. The attack source had a total of 859,756 unique IP addresses, indicating a high degree of distribution among attack sources. It can be assumed that many compromised devices worldwide were involved in the attack. This distribution is typical for modern DDoS attacks, in which cybercriminals often use botnets of IoT devices or insecure home routers. Here, the US was the main source of traffic, followed by China.
Traffic split by countries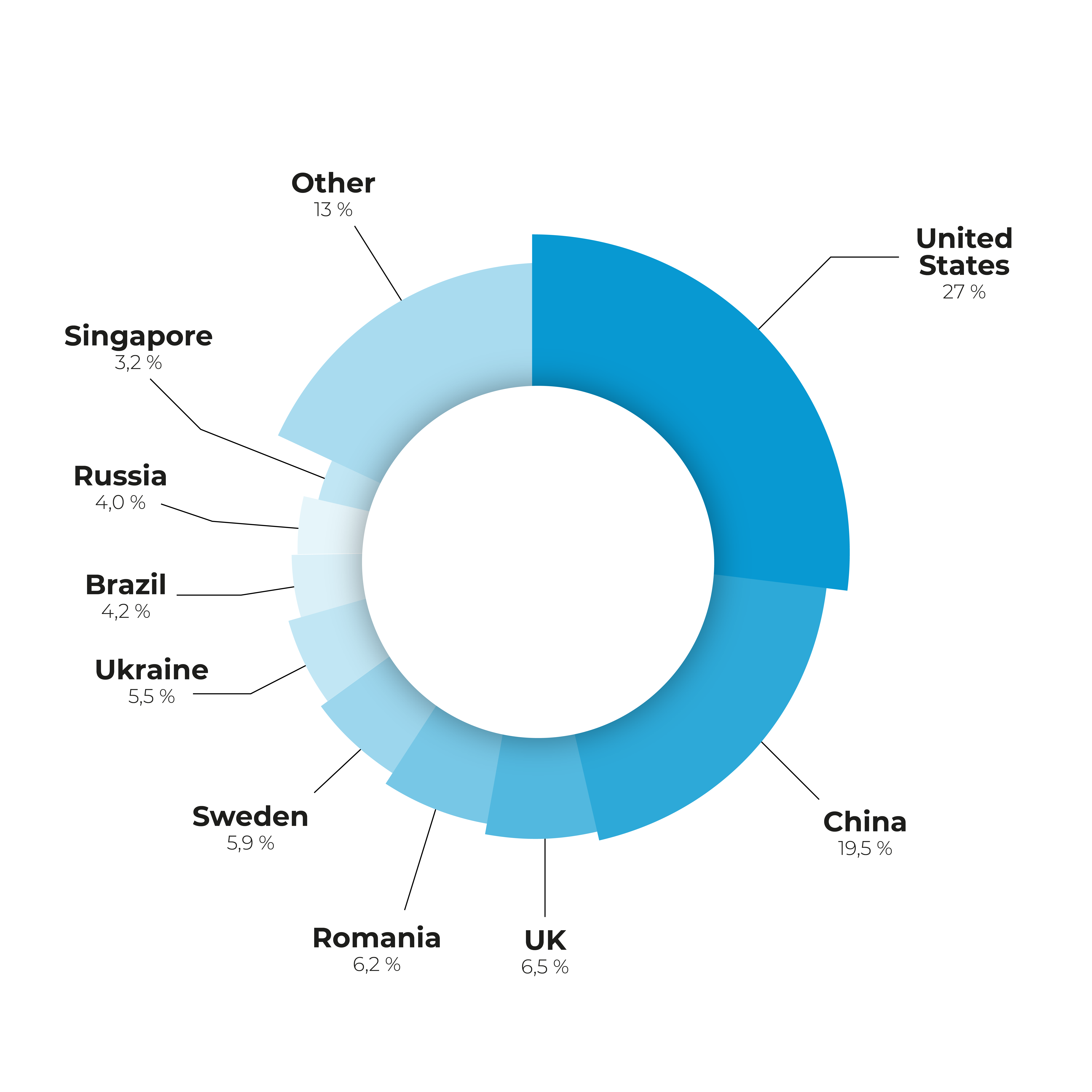
The breakdown of attack vectors is as follows:
- TCP (over 50% of the total attack volume): The use of randomly selected source ports and the targeting of destination port 80 (HTTP) suggests that the attackers were attempting to directly overload the targets web services.
- UDP (almost 40% of the volume): Since UDP packets are usually not connection-oriented, they are particularly suitable for attacks. They can be sent quickly and in large quantities without the need for a prior connection.
- ICMP accounts for about five percent of the attack volume. ICMP packets can be used to detect network connections, which suggests that the attackers may be trying to overload the network infrastructure.
- GRE: (around 5% of the volume): GRE tunnels are often used to transfer data over VPNs. This suggests that the attackers were attempting to disguise the GRE packets as a legitimate service and bypass filters and make their attacks more effective.
Attack Traffic in Mbps
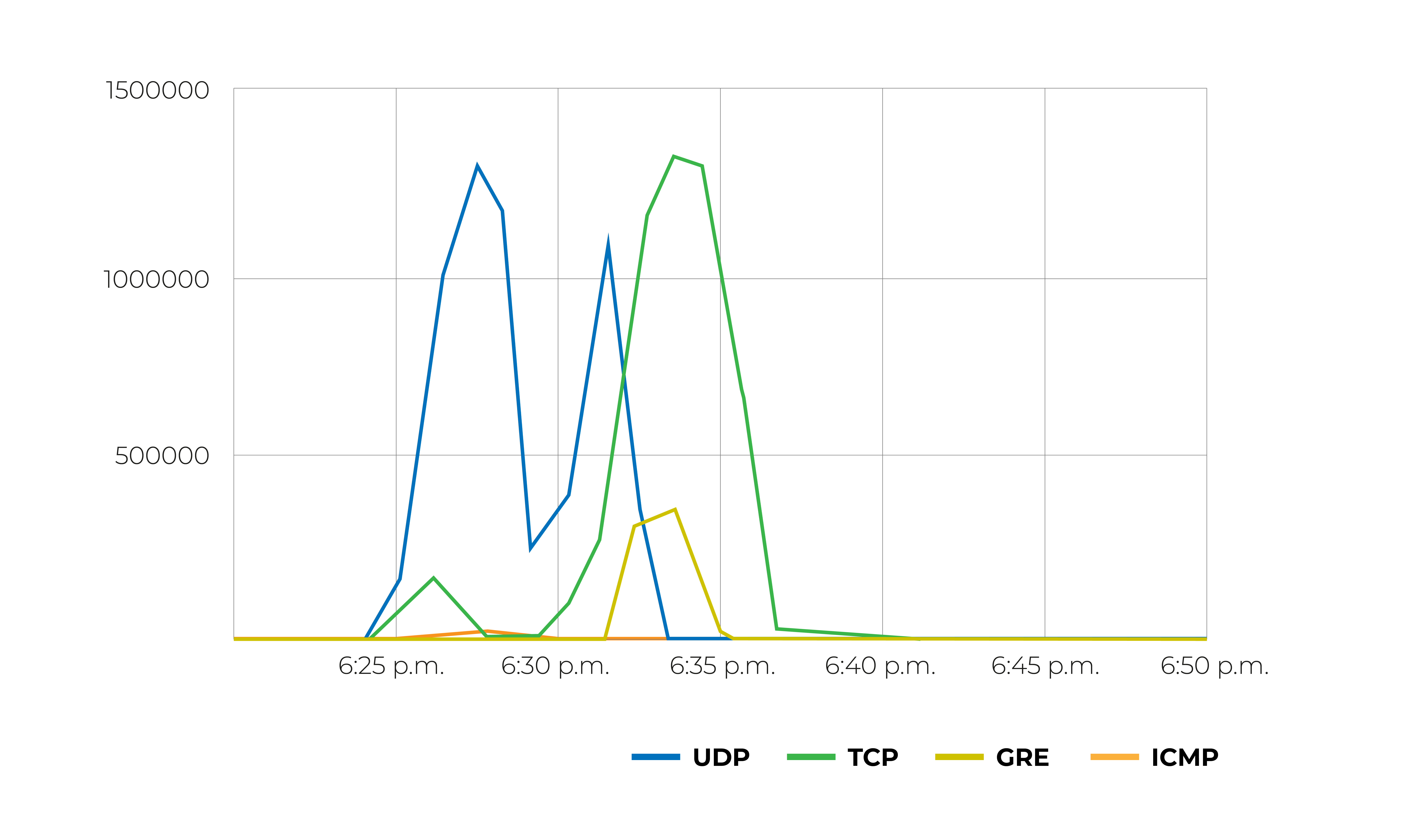
Dynamics of attack strategies
The dynamics of the attack strategies were particularly noteworthy. After about four minutes, the packet size of the attacks was significantly reduced. This is a tactical variation that cybercriminals often use to circumvent defenses. The subsequent increase in packet size for the TCP and UDP vectors and the moderate adjustment for GRE prove that the attackers are adapting their strategies in real time to the defenses of Link11.
Such a complex attack scenario can inevitably overload the target’s network capacity and server CPU. A successful attack would have brought digital business operations to a complete standstill. This would have had catastrophic consequences for many companies. The course of the attack clearly shows that DDoS defense strategies must be continuously optimized and adapted to changing threats.
Simple but effective attack strategies
The simplicity of the methods used – illegitimate web-based traffic connections – proves that attackers still frequently target the most widely used Internet service protocols and ports. These types of attacks remain popular among cybercriminals despite more advanced methods, because they are easy to generate. The attackers know full well that many target systems do not have the necessary capacity to deal with such attacks.
The strategic targeting of home ISP providers and the associated access/eyeball networks also shows how attackers exploit vulnerabilities on the internet. By infiltrating such networks, they can generate mass traffic that is usually difficult to identify and block.
Are you looking to enhance your resilience to cyber attacks? Our experts are available to provide guidance on how to optimise your IT security. Contact us for a solution tailored to your specific needs.
IoT devices and vulnerabilities – a dangerous combination
The increasing networking of devices and the Internet of Things (IoT) have changed the threat landscape.
Many devices are vulnerable to attacks because they operate without security measures. The attacks prove that we need to improve security standards. The recently discovered vulnerability CVE-2024-3080 illustrates the need to improve security standards in the IoT industry.
It occurs in certain ASUS router models. The “authentication bypass” vulnerability allows attackers to gain access to routers without entering valid credentials. Normally, access to a router’s configuration interface requires entering a username and password. However, this vulnerability allows attackers to bypass the authentication process. A compromised router becomes part of a botnet and is used to carry out DDoS attacks. This highlights the dangers associated with unsecured IoT devices.
Effective defense through global scrubbing centers
To counter such an attack, flexible defense mechanisms are essential. Link11 was able to fend off the attack thanks to its global network.
Each scrubbing center was able to analyze data streams and filter out malicious data. The scrubbing centers in Europe took on a large part. Distributing the data across different locations effectively spread the load. Link11’s automated filters and adaptive algorithms were key. Thanks to AI, we were able to block illegitimate traffic while continuing to process legitimate requests. This allowed us to carry out the defense without human intervention and without affecting the customer’s systems.
Conclusion
In an era when the threat of cyberattacks is constantly growing, organizations should implement robust, scalable, automated DDoS defenses to protect themselves from cyberthreats.
Automated systems are essential to detect and neutralize attacks in real time. The complexity and dynamics of today’s attacks require intelligent solutions based on machine learning that can adapt to new threats.
Employees and users must be trained in the use of IoT devices and made aware of the dangers. In addition, best security practices and regular updates are essential to close vulnerabilities and reduce attack vectors. Companies need to take action and arm themselves against the growing threats in cyberspace.
