Content

In a recent development, massive botnets have emerged, delivering unprecedented Distributed Denial-of-Service (DDoS) attacks, as described in this Ars Technica article. At Link11 we have seen and mitigated several attacks that are leveraging these types of botnets, with differing techniques and vectors but with the common characteristic of having massive capacity and scale.
Understanding Botnets and DDoS Attacks
A botnet is a network of compromised computers, often referred to as “zombies,” controlled by malicious actors. These networks are utilized to perform various cyber-attacks, including DDoS attacks, where multiple systems flood a target with excessive traffic, overwhelming its resources and rendering it inaccessible to legitimate users.
This particular botnet described in the Ars Technica article (dubbed Eleven11bot) has some defining components that allow it to realize unprecedented traffic levels, namely:
- Size – It’s estimated that Elevenbot is comprised of over 30k hosts (although there is still ongoing research to fully quantify the number of hosts). While there have been bigger botnets, it’s still a staggering number.
- Security experts believe that most of the compromised hosts are security cameras and webcams which have low security standards and capabilities for delivering high amounts of payload and packets per second
- Geographically Dispersed – the Botnet populates a high number of networks and countries, which allows it to diffuse and spread the surface area of the attack origins, before it aggregates on internet backbones, making it more difficult to isolate and identify each individual bot.
Link11 Findings and Observations
Link11 has encountered a few attacks that have the same characteristics, namely towards gaming platforms. Some of the notable aspects of the attack experienced:
- Massive Scale – The attacks observed are nearly 2 Tb/s and over 200 million packets-per-second at peak, exemplifying the industry trend of attacks simply getting larger and more frequent.

- Carpet Bomb Profile – The attacks rotated in targets and at one point was leveraging randomized source AND destination UDP ports, as well as wide range of packet sizes, against 4 Class C’s worth of ip space (over 1000 destination ip addresses) while achieving immense scale. This speaks to the sophistication and orchestration platform of the attack platform for overwhelming the target service/network.
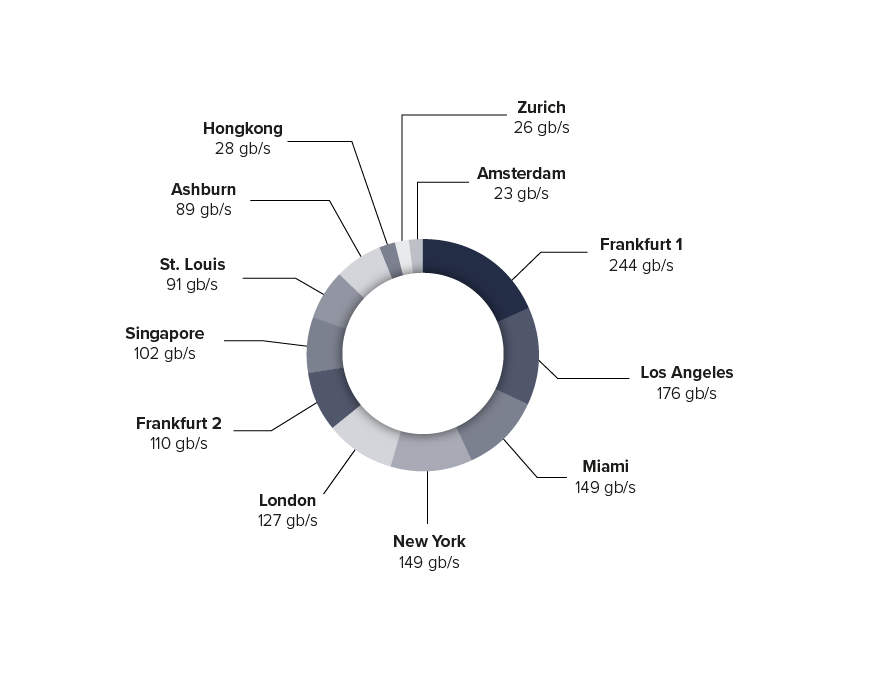
- Global Distribution – The global distribution of the botnet was illustrated in the attack towards the Link11 network. While there was a weighting towards N. American and European Pops, the diffusion even within these regions was eye catching; within just our Frankfurt POP’s alone we saw a significant distribution between the two data centers (see chart below). Also, there was a significant amount of traffic seen in our Asian nodes, which was not seen before in the Terabit attacks we have seen in the past:
Notable Botnet Incidents
Historically, botnets have been responsible for some of the most significant cyber-attacks:
- Mirai Botnet (2016): Exploited vulnerabilities in Internet of Things (IoT) devices, leading to massive DDoS attacks that disrupted major websites and services.
- Storm Botnet: Comprised of compromised Windows machines, it was known for its rapid propagation and resilience against countermeasures.
- Halloween 2024: Cloudflare reported a 5.6 Tb/s attack.
The Emergence of the New Botnet
The newly identified botnet distinguishes itself by its rapid assembly and the scale of its DDoS attacks. Within a short period, it has harnessed a vast number of devices, launching attacks that surpass previous records in size and intensity.
Implications and Response
The emergence of such a formidable botnet underscores the critical need for robust cybersecurity measures. Organizations and individuals must:
- Secure IoT Devices: Ensure that all internet-connected devices are updated with the latest security patches and are configured with strong, unique passwords.
- Implement Network Defenses: Deploy firewalls, intrusion detection systems, and DDoS mitigation services to protect against potential attacks.
- Stay Informed: Regularly monitor cybersecurity advisories and threat intelligence reports to remain aware of emerging threats.
As cyber threats continue to evolve, proactive and comprehensive security strategies are essential to safeguard digital infrastructures against such large-scale attacks.
Do you have any questions on this topic? Our cyber experts are at your disposal at any time.
